记录下,Virtualbox下如何实现主机和虚拟机之间文件夹共享及双向拷贝
关于双向拷贝
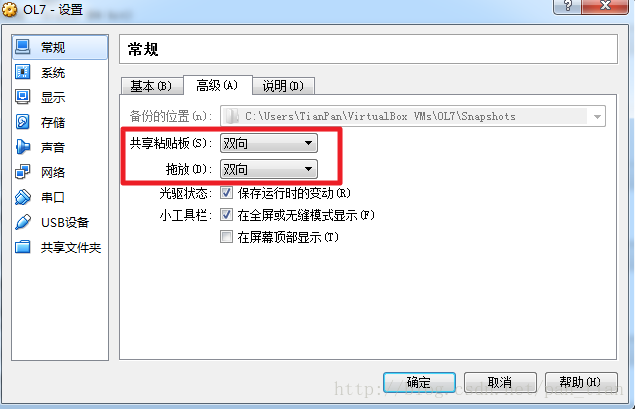
1.设置虚拟机为“双向”共享粘贴
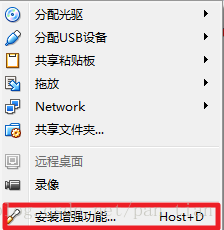
有的人反应只要设置双向粘贴就可以,但是我的不行,我还需要再给虚拟机安装一下增强功能。需要启动虚拟机,安装菜单项“设备”中的最后一项。
安装完增强功能,注意要重启虚拟机,双向拷贝才被启用。
关于文件夹共享
情况一:
Host操作系统:Windows 7
Guest操作系统:Windows Server
1.首先设置共享文件夹
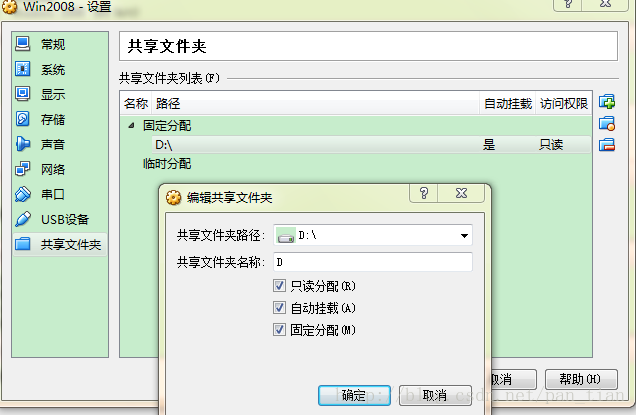
2.虚拟机中的菜单项中,设备 - 分配光驱 – 选择一个虚拟光盘。在弹出的对话框选择 VirtualBox 安装目录下选择
VBoxGuestAdditions.iso
3.虚拟机中的光驱,运行VBoxWindowsAdditions.exe,安装完成后,重启虚拟机中的系统,就能看到主机中的共享目录了。
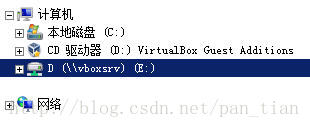
情况二:
Host操作系统:Windows 7
Guest操作系统:Oracle Linux
和情况一一样先设置共享目录。
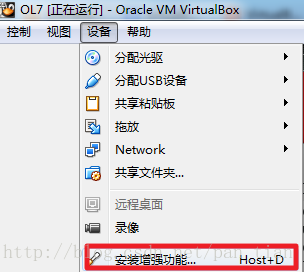
然后在Linux虚拟机上边的菜单中,设备->安装增强功能。
出现VBOXADDITIONS,然后运行此软件
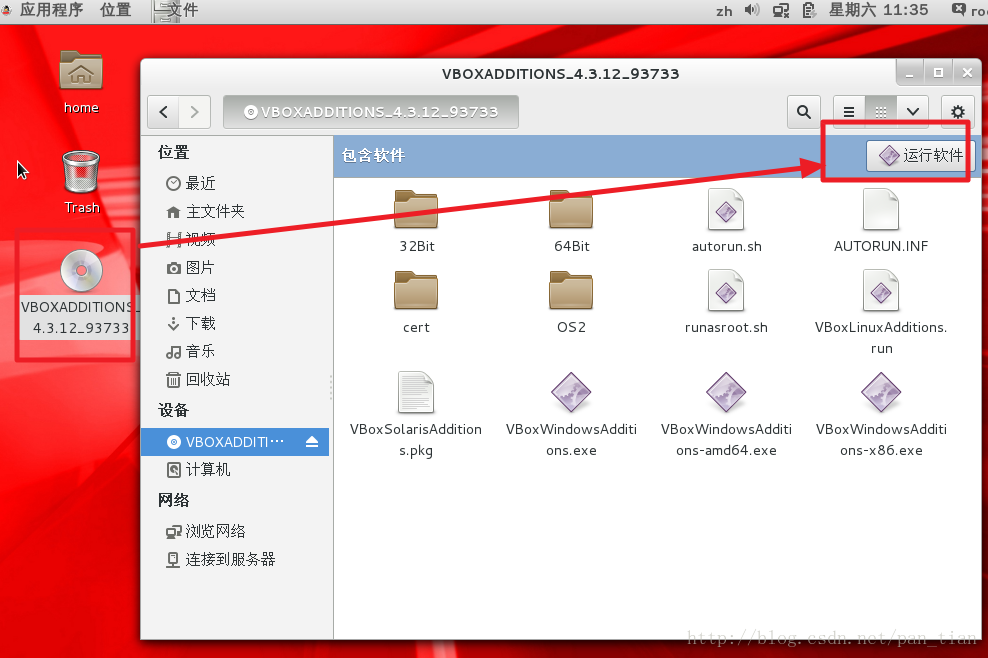
可以看到共享文件夹了
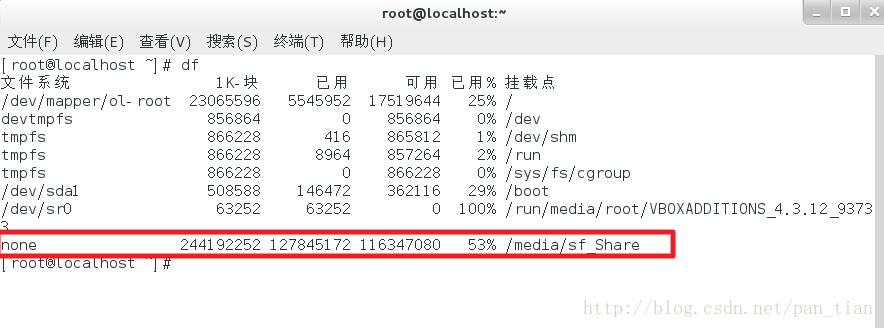
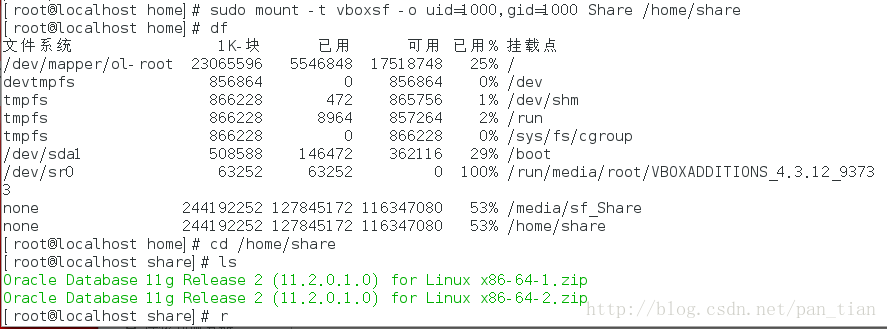
挂在这个目录到Linux本地目录。
首先创建一个文件夹
mkdir /home/share
改为可读可写
cd /home/share
chmod 777 .
运行命令加载
sudo mount -t vboxsf -o uid=1000,gid=1000 Share /home/share
红色Share为VirtualBox共享目录的名字
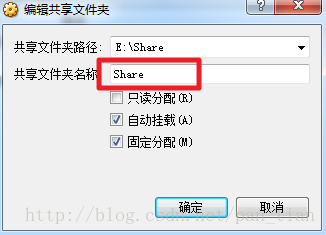
蓝色的/home/share为刚刚创建的目标目录。